Data’s role as a transformational business asset continues to grow. Thanks to increasing investments in application development; modern DevOps practices; and heightened business intelligence, analytics, and machine learning demands, nearly all businesses are accelerating data creation and usage. They are also scaling the number of locations that leverage data. This proliferation of data combined with mounting pressure to accelerate operations has led to an increase in the complexity of both IT infrastructure and IT operations.
Such factors put organizations and their infrastructures at great risk of experiencing malicious attacks, human error, and negligent behavior. Unfortunately, legacy strategies cannot adequately ensure that business operations will continue during and after these types of incidents. Companies can try to weave together capabilities in an attempt to prevent attacks and other breaches, but functional gaps, poor integration, and management complexity make meeting security objectives time-consuming and difficult.
Changing organizational mindsets from prevention to incident preparation—e.g., implementing storage solutions with built-in cyber resilience—is key to safeguarding critical data assets and being able to quickly respond to and recover from ransomware and other cyberattacks.
Introduction
IT faces new challenges. Nearly half (46%) of ESG survey respondents say IT is more complex today than it was two years ago. This increase in complexity may be the result of ongoing digital transformation initiatives (cited by 29%), higher data volumes (35%), the rapid evolution of the cybersecurity landscape (37%), and/or efforts to adhere to new data security and privacy regulations (32%).
Simultaneously, organizations are struggling to address a problematic shortage of critical IT skills. In fact, 48% of surveyed organizations report they don’t have enough cybersecurity specialists—it was the most often-cited shortage area. Additionally, these organizations are dealing with application, device, and remote/mobile worker sprawl, which are increasing the size and scope of the security perimeter that IT is tasked with protecting.
Given the complexity of modern IT, proliferating data, and ever-growing cyberattack threats, IT teams often struggle to keep pace. Trying to address complexity with internal personnel alone is a losing battle. Success requires modernizing the underlying infrastructure itself. However, when doing so, IT decision makers must look for technologies that don’t just meet application needs or simplify operations. Achieving true success means finding technology that can achieve those goals and improve the cyber-resiliency posture of the application environment as well.
The Rising Threat of Cyberattacks and Ransomware
Organizations face increasing cybersecurity threats, likely fueled by increasing financial incentives for cybercriminals. For example, complaints from the American public in 2020 to the FBI’s Internet Crime Complaint Center (IC3) increased 69% from 2019, with reported losses exceeding $4.1 billion.3 Additionally, over the past five years, the IC3 reports a combined $13.3 billion in total losses.4 As of the fourth quarter of 2020 in the U.S., the average length of interruption after ransomware attacks on businesses was 21 days.5 Clearly, ransomware’s negative impact on business operations is substantial.
A strong correlation exists between IT complexity and cyberattack vulnerability. As IT grows more complex, cyberattacks will increase in frequency and come at a higher cost.
Ransomware is a pervasive threat, and one that attacks a business’s most valuable asset—its data. The IC3 identified 2,474 reported ransomware incidents in 2020, and ESG found that 63% of the organizations it surveyed experienced ransomware attacks in the past year. In fact, 9% experienced ransomware attacks on a daily basis (see Figure 1).
Ransomware protection requires a technology strategy that expands beyond the realm of traditional cybersecurity—it should leverage advances in data storage and data protection as well.
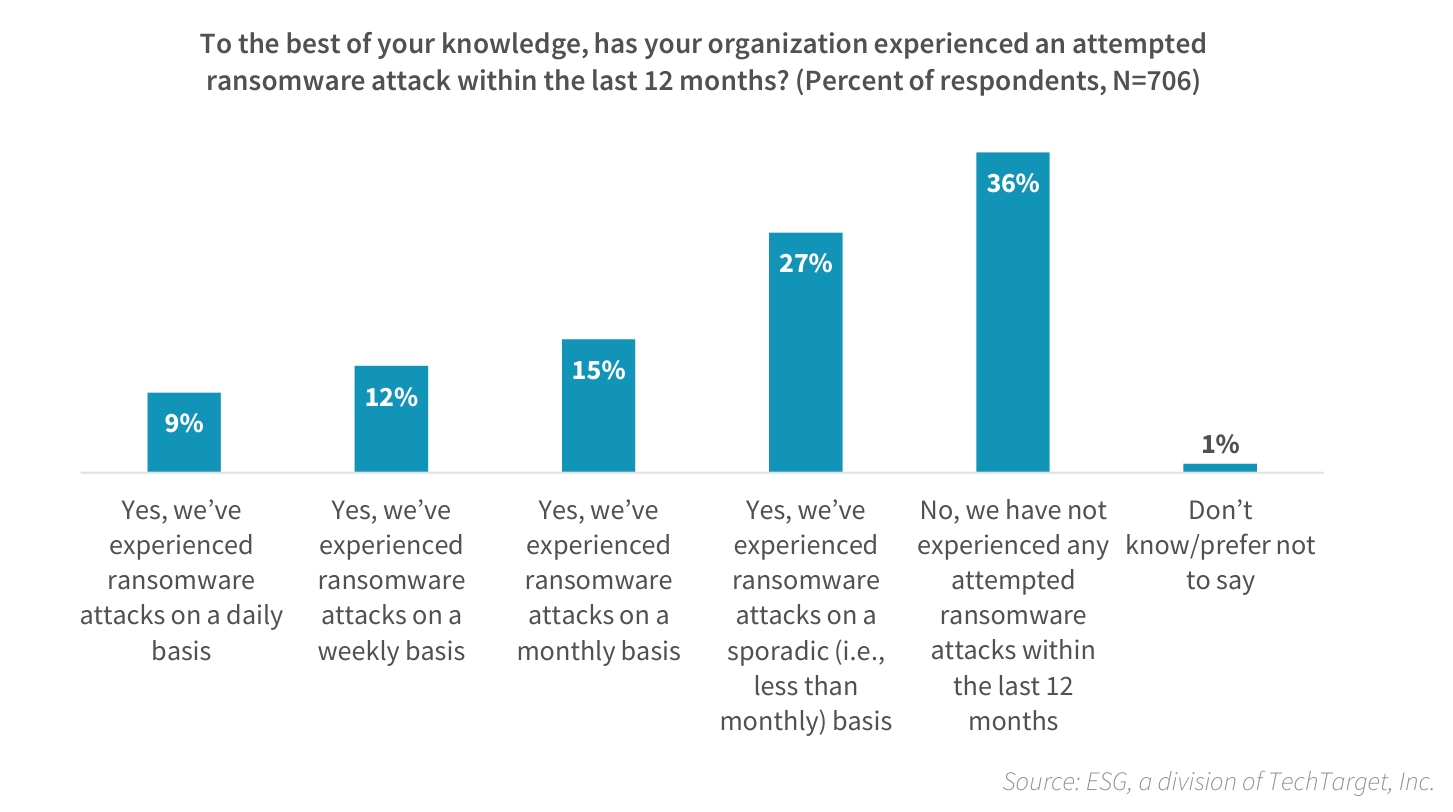
Sixty-three Percent of Respondents Experienced Ransomware Attacks in the Last 12 Months
The Role of Data Storage in Cyber Resiliency
Storage systems and storage administrators both play a big role in protecting against ransomware. When ESG asked IT decision makers which measures their organizations have in place to combat or mitigate ransomware attacks, 67% of the respondents reported using cyber tools for proactive ransomware avoidance, and 53% identified data recoverability capabilities such as air-gapping (see Figure 2).7 Those two commonly identified responses highlight the importance of not only implementing measures to avoid an attack, but also investing in solutions to ensure the business is prepared to recover when an attack inevitably occurs. It’s important to avoid simply setting up policies to combat or mitigate ransomware, and then stop. This “partial” approach creates a false sense of security because while effort is made to mitigate attacks, little or no effort is actually made to establish an effective data recovery plan before it’s needed.
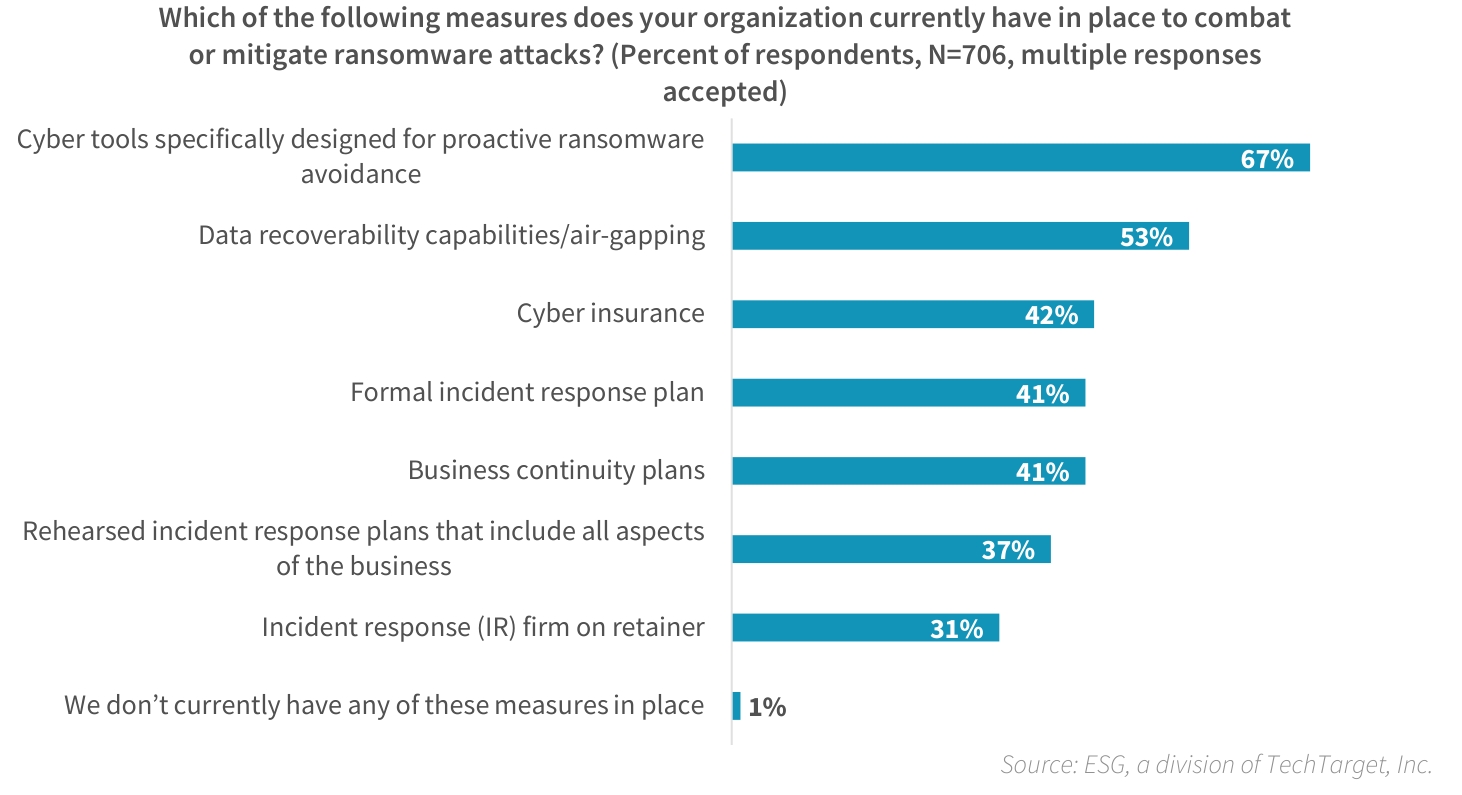
Common Measures in Place to Combat or Mitigate Ransomware
It’s important to remember that combating an attack is quite different from traditional data recovery. Typically, organizations almost always want to recover their data by using the most recent copy. But with ransomware, IT typically doesn’t know which “good” copy to use; hence, recovery is often riskier and can take much longer. Some ransomware attacks not only target data, but also target the backup infrastructure itself. This is why advanced storage capabilities are foundational for effective ransomware recovery.
While adopting the measures identified in Figure 2 is smart and needs to increase, organizations must understand that no single defense is 100% effective for ransomware recovery. While it is important to consider tools that specialize in identifying and avoiding ransomware as well as recovering data, that is just part of the effort. Even with the best defense, it’s possible an attack might get through. Organizations must prepare for that eventuality and assess how they can minimize the business impact by recovering as quickly as possible. To minimize overall ransomware exposure, organizations should look for ways to accelerate how soon they can identify attacks, how quickly they can mitigate any damage, and how fast they can recover with a known-good copy.
This is where strong cyber resiliency strategies come into play, taking into consideration all data-handling components, i.e., hardware, software, people, and process. When developing a cyber resilience posture, organizations should shift from asking “How do we protect?” to “If we’re hit by ransomware, how fast can we recover? How quickly can our business return to normal?”
Data Storage and Data Protection: Knowing Where to Focus to Minimize Ransomware Risk
Ransomware recovery is a form of disaster recovery, but the effects of ransomware are quite different from those of a fire or a flood. After all, you can generally tell when a fire is fully extinguished. Ransomware is more like a hidden spark inside a wall that could potentially reignite at any time. Storage admins need to focus on certain areas to help reduce the risks associated with ransomware. Because speed is essential, they should determine how quickly their organization can:
- Identify a risk.
- Quantify the damage that was done.
- Mitigate the damage by identifying a known-good copy, recovering using that known-good copy, and ultimately restoring operations.
Taking a “this won’t happen to us” approach is risky at best. Organizations must be proactive, and put in place an effective data storage and protection solution—before they actually need it.
Shifting from Cybersecurity to Cyber Resilience with IBM
With its extensive experience in cybersecurity and risk management, IBM is a recognized leader in cyber resilience and offers a comprehensive suite of advanced storage and data protection solutions, including:
- IBM FlashSystem, IBM Cloud Object Storage, and IBM Spectrum Scale, primary storage solutions that come with data immutability and encryption features.
- IBM Tape Storage, which also supports data immutability and encryption, and provides protection through air-gapping.
- IBM Spectrum Copy Data Management software manages and protects copies of data.
- IBM Spectrum Protect Suite for additional protection. Spectrum Protect software-defined storage can place data on flash, disk, object storage, and physical or virtual tape. It then detects malware and ransomware activity by identifying large deviations from normal access patterns.
- QRadar and Storage Insights solutions help accelerate detection of potential threats using AI-enhanced capabilities.
Cyber Resilience with IBM Cyber Vault
It is hard to overemphasize storage’s role in protecting against ransomware. The storage software is seeing the changes made to primary data, and because it is seeing those changes, it’s in a great position to identify when an attack is starting. It is the technology that is taking and protecting secondary copies, too—which makes storage critically important to help with recovery. With these facts in mind, perhaps one of the most useful tools of all in IBM’s cyber resiliency toolbox is IBM Cyber Vault.
IBM Cyber Vault is a security methodology for rapid recovery from a cyberattack. It is built on top of IBM Safeguarded Copy, a technology for regularly creating isolated, immutable snapshots. Cyber Vault analyses these snapshots looking for potentially malicious changes, which could indicate the presence of ransomware. IBM Cyber Vault also integrates with IBM QRadar and IBM Storage Insights for even faster detection. Its validation of immutable copies allow admins to quickly identify a good copy, test it, and then restore from it.
In terms of enhancing speed in particular, IBM Cyber Vault helps storage administrators accelerate:
- Identification—The integration of QRadar and Storage Insights offers enhanced detection and monitoring.
- Mitigating and quantifying damage—This is an automated process. Early, automatic detection of attacks obviously enables faster recovery from them.
- Identification of a known-good copy—Automation of immutable copies of data occurs if a threat is detected.
- Restoration of operations—Rapid recovery is possible within hours, instead of days or weeks (see Figure 3).
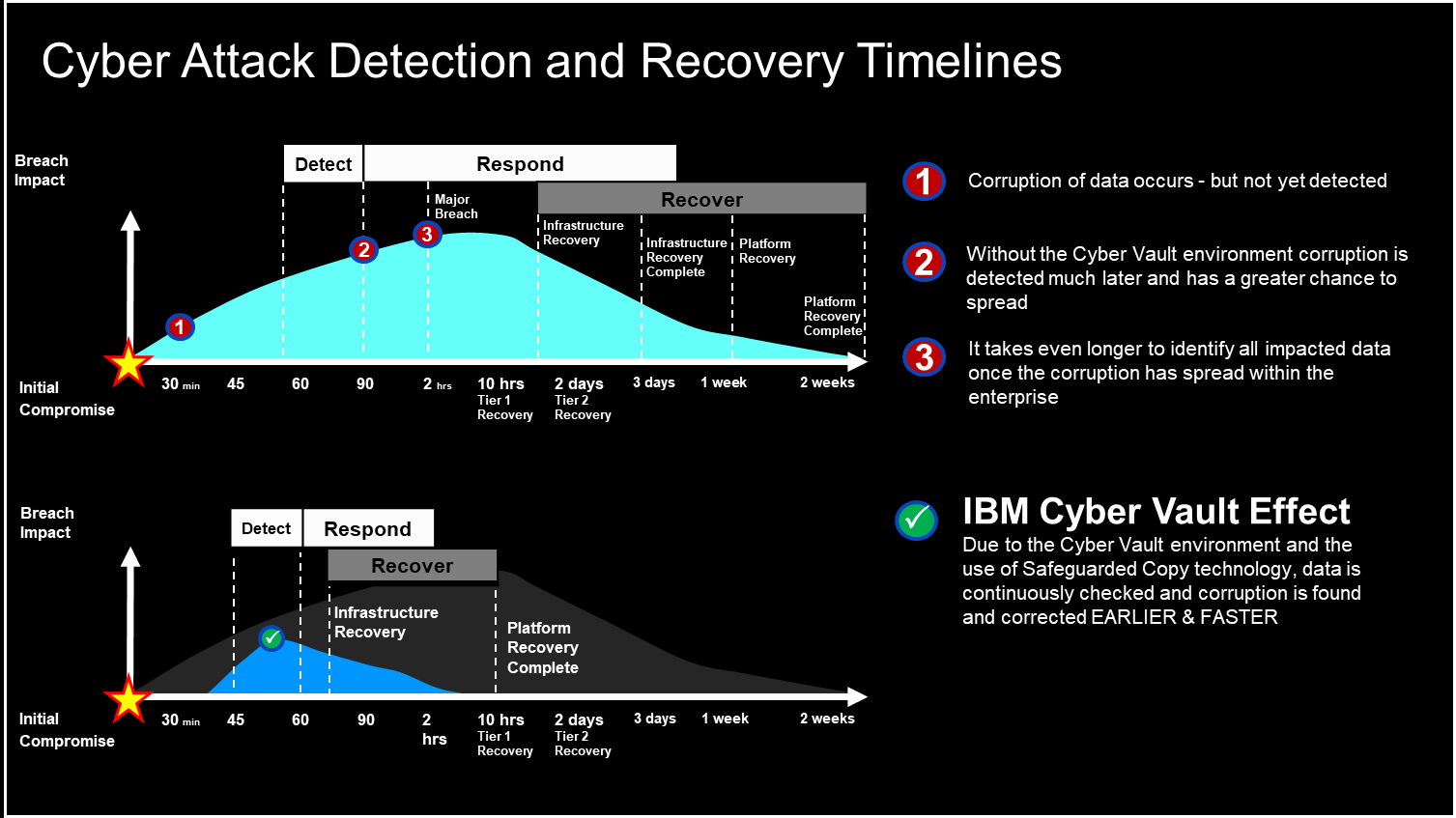
Common Measures in Place to Combat or Mitigate Ransomware
The Bigger Truth
IT infrastructures are continuing to become more complex, increasing the opportunity for human error, system failures, or negligence to occur. Simultaneously, malicious actors—both inside and outside the organization—are relentless in their efforts to search for and exploit weak links.
Without a doubt, security incidents will happen. This fact should compel a change in the organizational mindset from reactive to proactive—from fervently attempting to prevent an attack to preparing for and responding to security failures when they happen. This is the transformation organizations must undertake as they travel from cybersecurity to cyber resilience.
Many organizations are modeling their cyber resilience strategies after the guidance provided by the NIST Cybersecurity Framework, which recommends that organizations identify critical resources, protect those resources, detect failures and breaches, and plan for response and recovery from cyber incidents. Leading organizations are paying special attention to IT infrastructure capabilities that can enhance their cyber resilience through capabilities such as data discovery, copy management, encryption, access control, and immutable storage, while maintaining multiple data recovery options.
For IT and business leaders, cyber resilience is all about making the right technology decisions and the right business decisions—with the goal of keeping the business operational.



